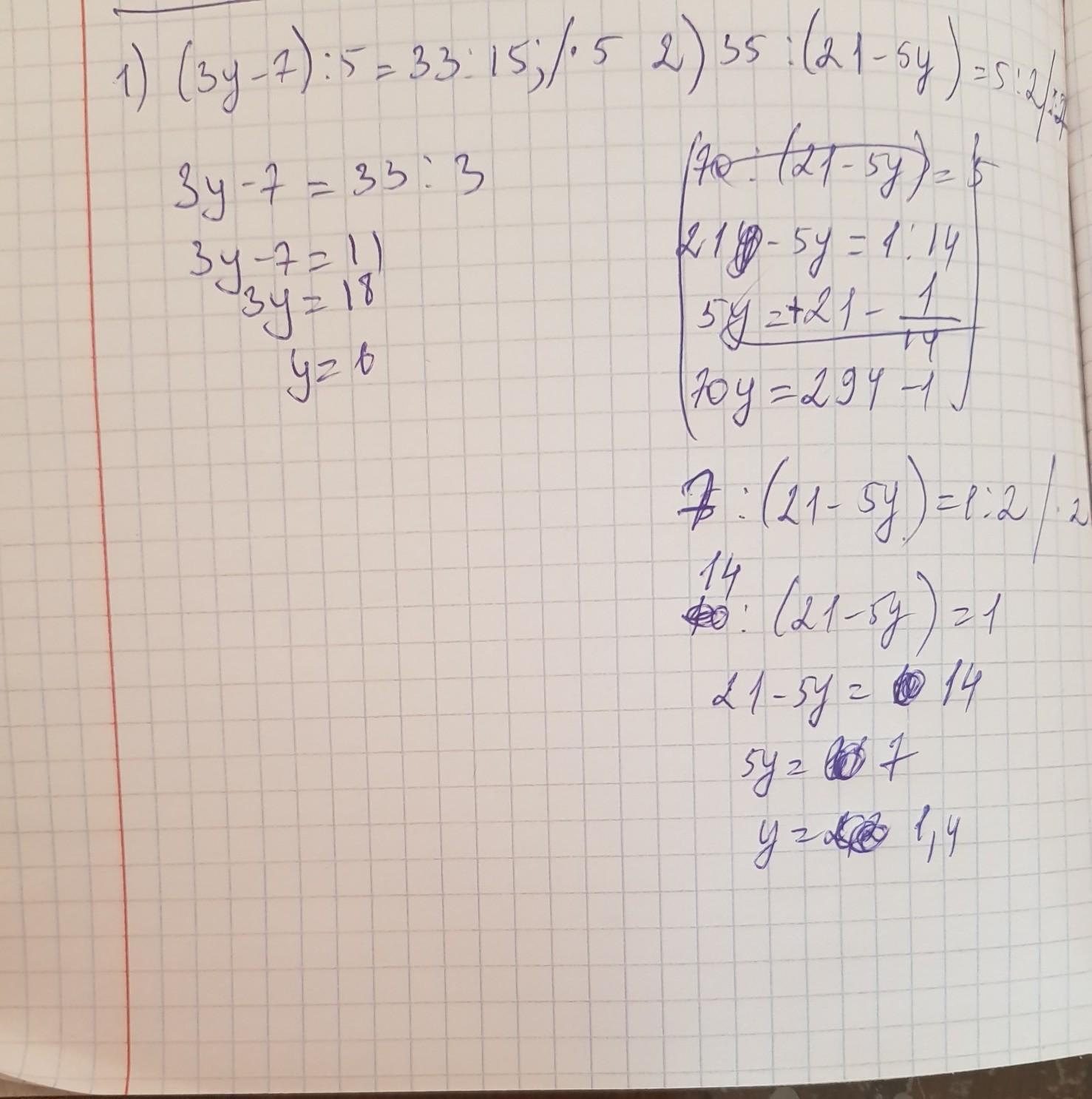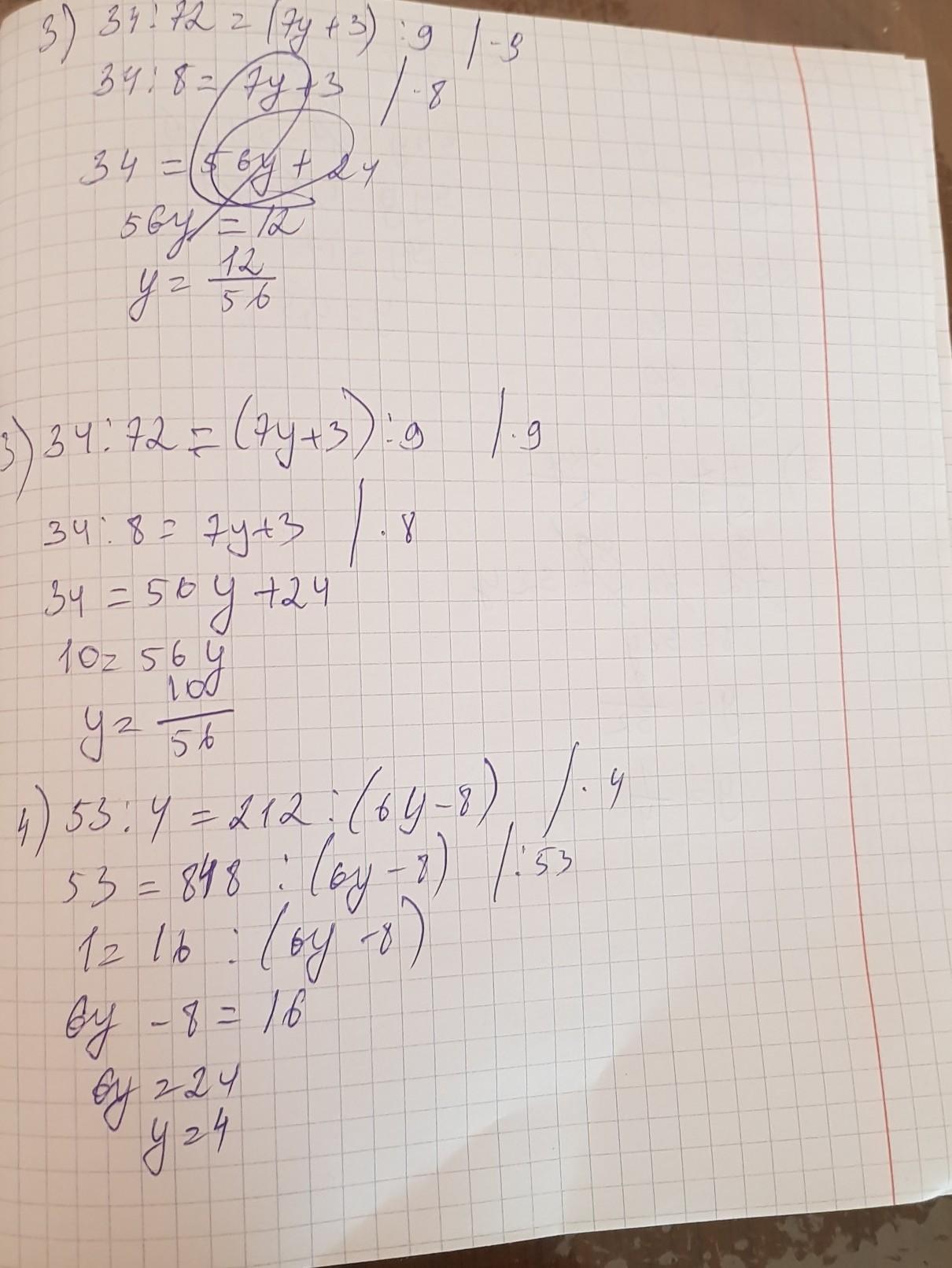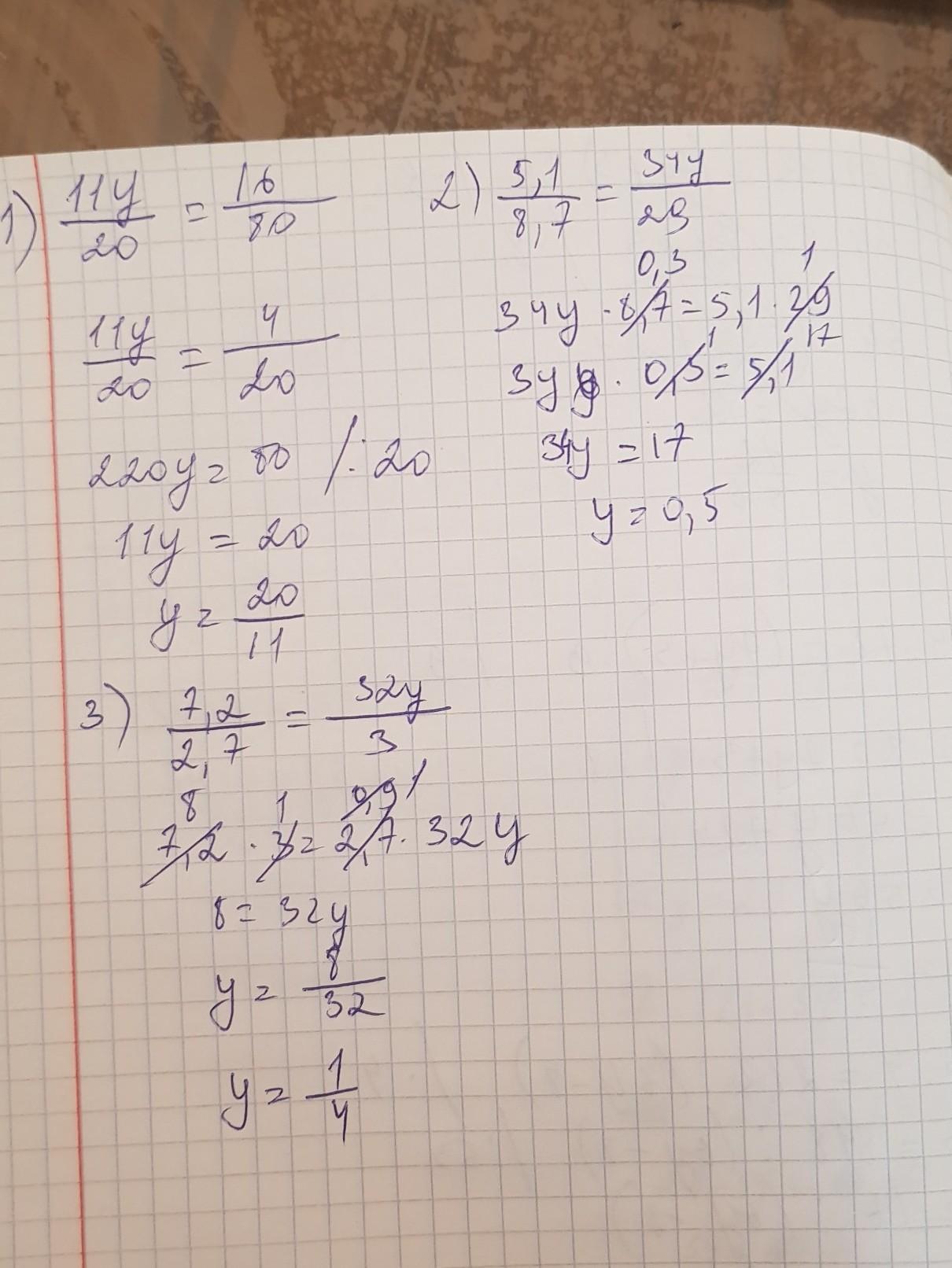математика.
помогите пажалуста

Ответы
Ответ:
Пошаговое объяснение:
1)
(3y - 7) : 5 = 33 : 15
15*(3y - 7) = 33*5
45y - 105 = 165
45y = 165+105
45y = 270
y = 270:45
y = 6
-------------------
2)
35 : (21 - 5y) = 5 : 2
5*(21 - 5y) = 35 * 2
105 - 25y = 70
25y = 105 - 70
25y = 35
y = 35 : 25
y = 1,4
------------------
3)
64 : 72 = (7y + 3) : 9
72*(7y + 3) = 64 * 9
504y + 216 = 576
504y = 576 - 216
504y = 360
y = 360 : 504
y = 5/7
-----------------------
4)
53 : 4 = 212 : (6y - 8)
53 * (6y - 8) = 212 * 4
318y - 424 = 848
318y = 848 + 424
318y = 1272
y = 1272 : 318
y = 4
-----------------
1)
11y/20 = 16 : 80
11y * 80 = 20*16
880y = 320
y = 320 : 880
y = 4/11
-----------------------
2)
5,1 : 8,7 = 34y/29
34y * 8,7 = 29 * 5,1
295,8y = 147,9
y = 147,9 : 295,8
y = 0,5
-------------------------
3)
7,2 : 2,7 = 32y/3
32y * 2,7 = 7,2 * 3
86,4y = 21,6
y = 21,6 : 86,4
y = 0,25
Пошаговое объяснение:
влвлворараиаивививиивививиытыоыо